Oracle Database Cloud Service (DBCS) uses Oracle Transparent Data Encryption (TDE) to protect data at rest for its databases. TDE is a two-tier key architecture comprising data encryption and master encryption keys. The data encryption keys that protect the tablespaces are stored within the database but are wrapped by a single master encryption key. In the case of Oracle-managed keys, the master keys are stored in an Oracle Wallet - a PKCS#12 standard-based key store file - on the filesystem of the DBCS system outside of the database.
We are pleased to announce the general availability of Database Cloud Service (DBCS) integration with the OCI Vault service. Users now have the control to create and manage TDE master keys within the OCI Vault that protect their DBCS VM databases. With this feature, users have the option to continue keeping the TDE master encryption keys in Oracle-managed file-based encryption on the DB System or use the OCI vault service to store and manage the master encryption keys. The OCI Vault keys used for protecting databases are stored in a highly available, durable, and managed service.
With OCI Vault integration with DBCS, customers can now
◉ Centrally control and manage TDE master keys by enabling OCI Vault based key encryption while provisioning Oracle databases on DBCS.
◉ Have their TDE master keys stored in a highly available, durable, and managed service wherein the keys are protected by hardware security modules (HSM) that meet Federal Information Processing Standards (FIPS) 140-2 Security Level 3 security certification.
◉ Rotate their encryption keys periodically to maintain security compliance and, in cases of personnel changes, to disable access to a database.
◉ Migrate from Oracle-managed keys to customer-managed keys for their existing databases.
◉ Bring in their own keys, that's BYOK (Bring Your Own Key), and use them while creating databases with customer-managed encryption.
Databases using customer-managed encryption support VM DB System cloning, in-place restore, out-of-place restore, intra-region Data Guard configuration, and PDB specific operations like PDB creation and local cloning.
OCI Console Experience
Let's take a look at the OCI Vault integration for DBCS using the OCI console:
◉ Enable customer-managed encryption during database provisioning
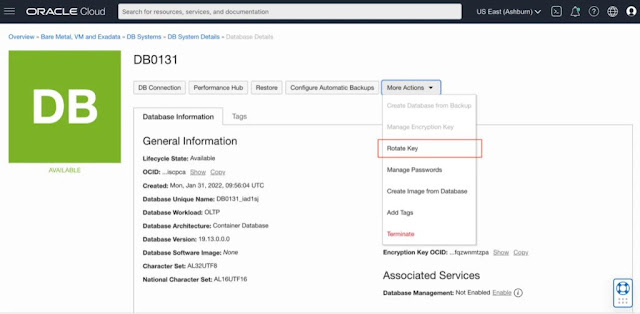
◉ View the encryption method being used for the database
◉ Rotate customer-managed key
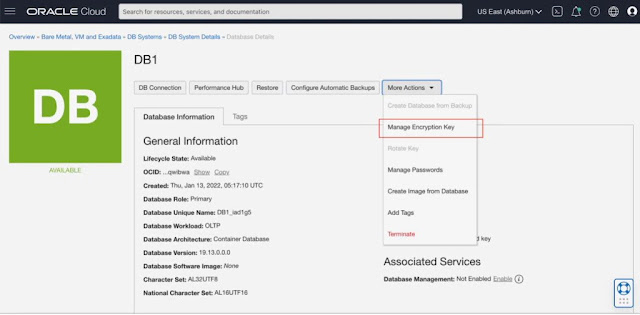
◉ Migrate from Oracle-managed key to customer-managed key
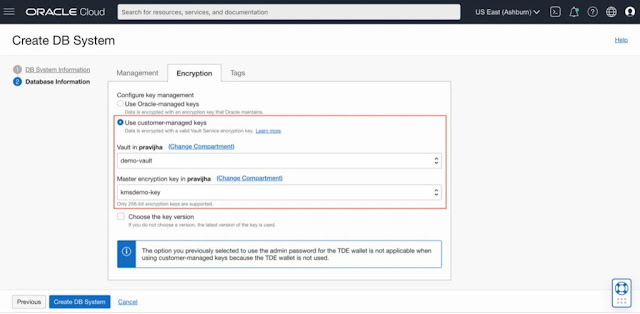
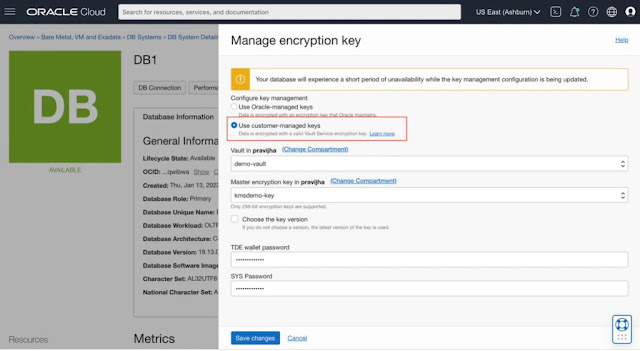
In order to use customer-managed keys with the DBCS VM database, you should first access the OCI Vault service, and create a Vault, and an encryption key. The key protection method can either be HSM (Hardware Security Module) or Software. The encryption key algorithm you use must be AES-256.
Next, you should ensure the required IAM policy is set for the DB System to access the Vault and managed keys. Once these prerequisite steps are complete, you can create a DBCS VM database protected by customer-managed keys.
Enable ustomer-managed encryption during database provisioning
From the Bare Metal, VM, and Exadata service home page, navigate to DB Systems and click on 'Create DB System'. Fill in the DB System-specific details, and go to the 'Database Information section. At the bottom of the page, click on 'Show Advanced Options' and go to the 'Encryption' tab. Choose 'Use customer-managed keys' which enables your data to be encrypted with a Vault service encryption key. Choose a Vault and a Key from the dropdown. Optionally you can choose a key version especially if you want to bring your on-premise keys to the cloud. If you don't choose that, the latest version of the key is used for encryption.




0 comments:
Post a Comment