Network perimeter security is the primary method for securing cloud resources. This is generally done by creating virtual networks/subnets, security lists and firewalls. For Oracle multi-tenant databases deployed on Exadata Cloud@Customer, there is now an additional layer of network security available. Access Control Lists at the pluggable database level. What this means is that while the Exadata Infrastructure may be deployed in a private customer subnet and access is governed by the security rules associated with that subnet, each ADB or pluggable database can have its own set of access rules. This is done by defining an Access Control List at the time of provisioning an ADB or at a later stage if desired. Access Control Lists can be one or more IP addresses or a CIDR block.
Typically, an Autonomous Container Database (ACD) may have multiple Autonomous Databases (ADB) providing a higher degree of consolidation and cost efficiency by leveraging service features such as online auto-scaling. By defining Access Control Lists (ACL) for each ADB, you now have much better control on which specific SQL clients or users can access the database.

As an example, take the Exadata Cloud@Customer deployed in a customer data center in a private network with CIDR 10.22.0.0/16. The network security rules may be setup to allow traffic from any host within this corporate network but by setting up ACLs at the database level you can now allow / disallow traffic from specific applications or client users. This has other security benefits such as, say,
a.) blocking ad-hoc users from accessing production databases directly ( even if they have the right credentials)
b) Allowing client connections to certain databases from office locations only ( although I cannot imagine such an ACL rule in these times)
c) If you are providing Database as a Service to your organization using Autonomous ( which is a great use case btw) then each database can be associated with a line of business / application / project team etc.
Let's take a look at how to go about setting up ACLs.
We'll look at doing this from the database console in Oracle Cloud Infrastructure but you can easily automate the process using a robust set of REST APIs available for each action.
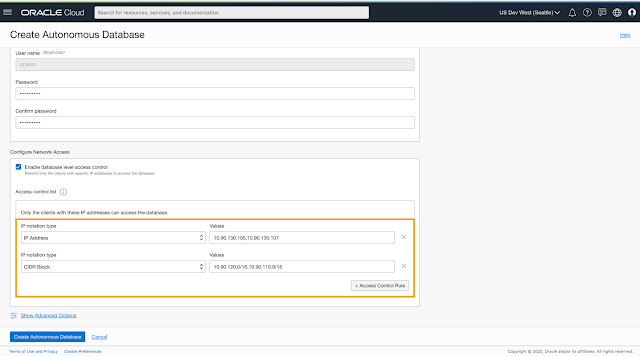
1. Set up ACLs at the time of your Autonomous Database provisioning
You are provided the choice to enable network ACLs on the provisioning page as shown below.

Next, you simply provide your list of IP Addresses or CIDR ranges to allow connections from.
Make sure you do not leave this list empty once your enable ACLs or else your database may be inaccessible ( although you can always come back and edit this)
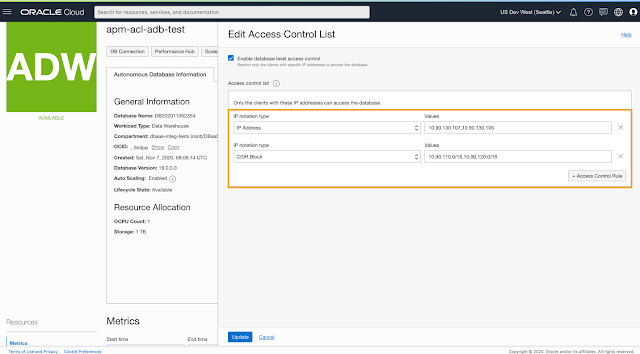
2. Setup or modify ACLs for existing ADBs
If you wish to setup ACLs for your already existing databases or change a rule later, you can easily do that from the database console
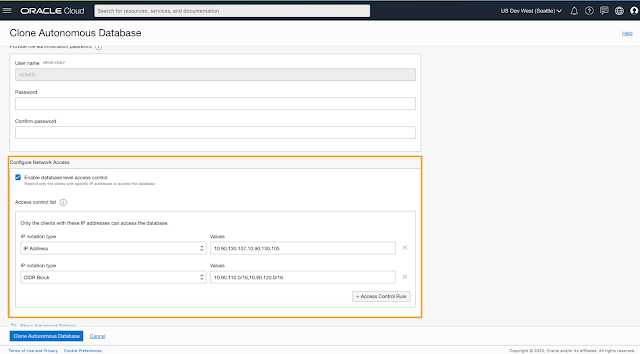
... and in the event you clone your database ( a nifty feature in Autonomous) , your ACLs carry over to the clone and once again, you may edit them as desired.
Source: oracle.com





0 comments:
Post a Comment