“There should be no on/off button for security, it should always be on, everything should always be encrypted – there should be no option to turn security off” – Larry Ellison
If you would like to check how secure your Oracle database it, just run the free tool called Oracle Database Security Assessment Tool (DBSAT)!
First, download it for free from MOS Doc ID 2138254.1. Check also the DBSAT documentation.
The Oracle Database Security Assessment Tool is a simple command line tool showing how securely your database is configured, who are the users and what are their privileges, what security policies and controls are in place, and where sensitive data resides with the goal of promoting successful approaches to mitigate potential security risks.
DBSAT has three components: Collector, Reporter, and Discoverer.
Here are the steps of how to produce the report in Oracle Database 20c. DBSAT supports also Oracle Database versions Oracle 10.2 through Oracle 19c.
1. Make sure first you have zip, unzip and python on the database server:
[root@dbexam ~]# id
uid=0(root) gid=0(root) groups=0(root)
[root@dbexam ~]# cd /home/oracle/
[root@dbexam oracle]# yum install -y zip unzip python
Loaded plugins: ulninfo, versionlock
mysql-connectors-community | 2.6 kB 00:00
mysql-tools-community | 2.6 kB 00:00
mysql80-community | 2.6 kB 00:00
ol7_UEKR5 | 2.5 kB 00:00
ol7_latest | 2.7 kB 00:00
(1/3): mysql-connectors-community/x86_64/primary_db | 68 kB 00:00
(2/3): mysql80-community/x86_64/primary_db | 128 kB 00:00
(3/3): mysql-tools-community/x86_64/primary_db | 83 kB 00:00
(1/5): ol7_UEKR5/x86_64/updateinfo | 41 kB 00:00
(2/5): ol7_UEKR5/x86_64/primary_db | 7.6 MB 00:00
(3/5): ol7_latest/x86_64/updateinfo | 3.1 MB 00:00
(4/5): ol7_latest/x86_64/group | 660 kB 00:00
(5/5): ol7_latest/x86_64/primary_db | 30 MB 00:00
Excluding 262 updates due to versionlock (use "yum versionlock status" to show them)
Package zip-3.0-11.el7.x86_64 already installed and latest version
Package unzip-6.0-20.el7.x86_64 already installed and latest version
Package python-2.7.5-86.0.1.el7.x86_64 already installed and latest version
Nothing to do
[root@dbexam oracle]#
2. Create a database user for running the Security Assessment Tool. You can also run it as sysdba but I would rather have a separate user:
create user dbsat_user identified by dbsat_user;
grant create session to dbsat_user;
grant select_catalog_role to dbsat_user;
grant select on sys.registry$history to dbsat_user;
grant select on sys.dba_users_with_defpwd to dbsat_user;
grant select on audsys.aud$unified to dbsat_user;
grant audit_viewer to dbsat_user;
grant capture_admin to dbsat_user;
grant dv_secanalyst to dbsat_user;
3. Run the tool:
[oracle@dbexam dbsat]$ ./dbsat collect dbsat_user/dbsat_user@//localhost:1521/xxxxx.oraclevcn.com dbsat_output
Database Security Assessment Tool version 2.2.1 (May 2020)
This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation,
any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies.
Connecting to the target Oracle database...
SQL*Plus: Release 20.0.0.0.0 - Production on Tue Nov 10 08:35:00 2020
Version 20.2.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Connected to:
Oracle Database 20c EE High Perf Release 20.0.0.0.0 - Production
Version 20.2.0.0.0
Setup complete.
SQL queries complete.
.......
OS commands complete.
Disconnected from Oracle Database 20c EE High Perf Release 20.0.0.0.0 - Production
Version 20.2.0.0.0
DBSAT Collector completed successfully.
Calling /u01/app/oracle/product/20.0.0/dbhome_1/bin/zip to encrypt dbsat_output.json...
Enter password:
Verify password:
adding: dbsat_output.json (deflated 88%)
zip completed successfully.
[oracle@dbexam dbsat]$
4. Generate the report:
[oracle@dbexam dbsat]$ ./dbsat report dbsat_output
Database Security Assessment Tool version 2.2.1 (May 2020)
This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation,
any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies.
Archive: dbsat_output.zip
[dbsat_output.zip] dbsat_output.json password:
inflating: dbsat_output.json
DBSAT Reporter ran successfully.
Calling /usr/bin/zip to encrypt the generated reports...
Enter password:
Verify password:
zip warning: dbsat_output_report.zip not found or empty
adding: dbsat_output_report.txt (deflated 78%)
adding: dbsat_output_report.html (deflated 84%)
adding: dbsat_output_report.xlsx (deflated 3%)
adding: dbsat_output_report.json (deflated 82%)
zip completed successfully.
5. Extract (for example) the .html file:
[oracle@dbexam dbsat]$ unzip dbsat_output_report.zip
Archive: dbsat_output_report.zip
[dbsat_output_report.zip] dbsat_output_report.txt password:
inflating: dbsat_output_report.txt
inflating: dbsat_output_report.html
inflating: dbsat_output_report.xlsx
inflating: dbsat_output_report.json
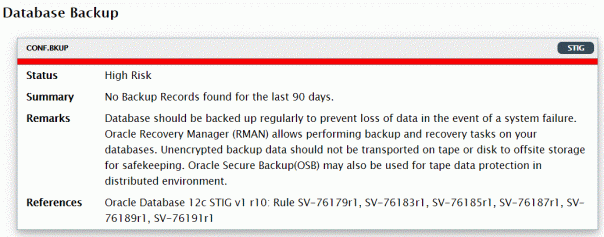
6. View the report, note that most areas will probably be in PASS status, some will be with LOW RISK, some might be even classified as HIGH RISK:
Although in ADB we have no OS access, you can still run the Database Security Assessment Tool.
You need to have the Instant Client installed and then use the ADMIN database user from Autonomous DB.
Clearly, you will get “ORA-20002: Complete without OS Commands” as the execution of the Collector was on the client server instead of on the underlying DB server to which we have no access.
DBSAT on Youtube:
Source: juliandontcheff.wordpress.com






0 comments:
Post a Comment