One of our design goals for Oracle Audit Vault and Database Firewall is to continue to provide an enterprise-class solution that takes much of the complexity out of database activity monitoring and database security posture management. With that goal in mind, Audit Vault and Database Firewall (AVDF) 20 Release Update 11 (20.11) continues to expand support for enterprise-class features along with significant improvements in usability and operations.
Here is what’s new in the latest AVDF Release:
- QuickCSV audit collector
- Integration with identity provider for single-sign-on
- Revamped alert UI workflow
- Fleet-wide security assessment drift chart
- Expanding support for tracking before/after values
- Finely scoped database firewall policies and reports
- Use of global sets in all activity and GDPR reports
- Audit trail migration
- AVDF certificate rotation from UI
Now, let's review some of those in detail.
QuickCSV audit collector
AVDF supports out-of-box audit log collection from multiple target types, including relational databases such as Oracle, Microsoft SQL Server, IBM DB2, MySQL, and PostgreSQL. AVDF also collects audit records from non-database targets, including operating system audit records for Windows, AIX, Sparc, and Solaris, as well as Microsoft Active Directory. However, there is a variety of systems that produce audit records, and this is where AVDF’s custom collector framework helps by collecting audit records available from database tables via RESTful API or audit data stored in JSON, CSV, and XML file formats.
We have seen that comma-separated value (CSV) is one of the most popular audit log formats used in applications, databases, and infrastructure components. With the new QuickCSV Collector in AVDF 20.11, you can easily import CSV audit files and map them to the AVDF audit schema as a one-time task. Once mapping is complete, audit data will be collected periodically from the CSV audit files like any other supported targets.
For example, you may use the QuickCSV collector to collect audit data from MariaDB, EnterpriseDB (Postgres), and other databases that create audit data in CSV. This approach helps you generate audit reports and alerts and protect and manage audit logs.
Figure 1: QuickCSV collector
Integration with identity provider for single-sign-on
Today, many of you implement single sign-on (SSO) using an enterprise identity service for your applications to minimize account proliferation and authentication mechanisms. Now, with AVDF 20.11, you can integrate with identity providers (IdP) such as Azure, Active Directory Federation Services, and Oracle Access Manager through SAML 2.0 integration. After integrating AVDF with your IdP, AVDF console users can be authenticated by your IdP using SSO.
With this new feature, you have multiple options to choose from as your authentication method:
- Users authenticated with SSO – added in 20.11
- Users in a centralized directory like Microsoft Active Directory or OpenLDAP
- Users authenticated using local passwords in AVDF
Figure 2: AVDF authentication methods
Revamped alert UI workflow:
We know most organizations are concerned about data breaches and ransomware, but when prevention fails, we need to help you understand what happened and detect attempts quickly. A better alert policy workflow contributes to a better detection system.
AVDF’s alert policy creation is completely revamped in AVDF 20.11, providing an intuitive and user-friendly experience. New alert policies can be created with just a few clicks through pre-defined templates or by modifying existing policies with new conditions.
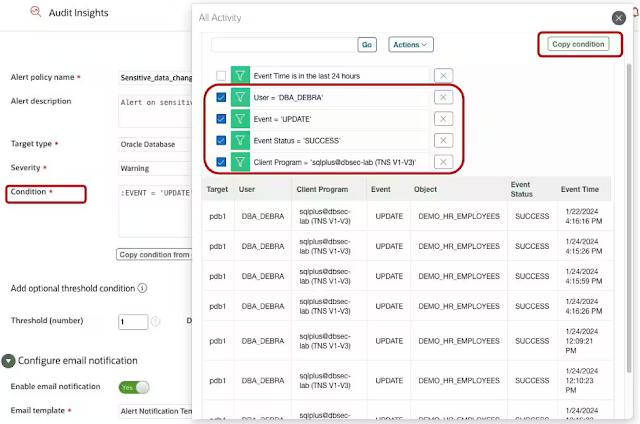
AVDF’s unique interactive reporting capability allows customers to quickly slice and dice the data to reach that one record of interest, and now this capability is available in the alert policy as well. You can also use the interactive report filters to define complex conditions for which alerts can be raised. In the example below, if you want to receive an alert when a privileged user updates sensitive data directly from SQLPlus, you can simply apply filters to your report and copy that to create the alert condition.
Figure 3: Alert policy condition using report filters
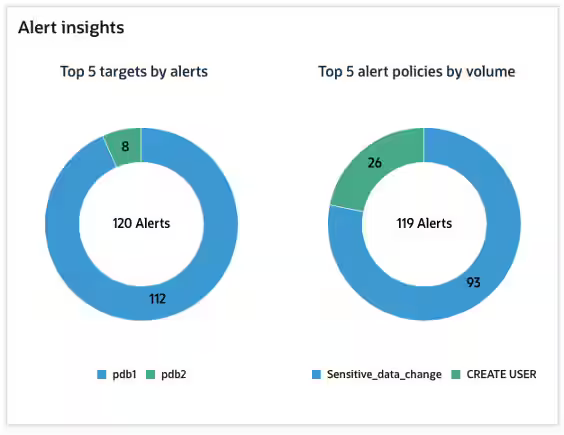
You can get a quick view of all the alerts generated on the alert policy page without going away from the alert definition, improving the overall user experience of alert usability. In addition, we made it much easier to notify the recipients of any alerts raised. Now, your auditor dashboard provides multiple actionable insights on the generated alerts.
Figure 4: Alert Insights
Fleet-wide security assessment drift chart
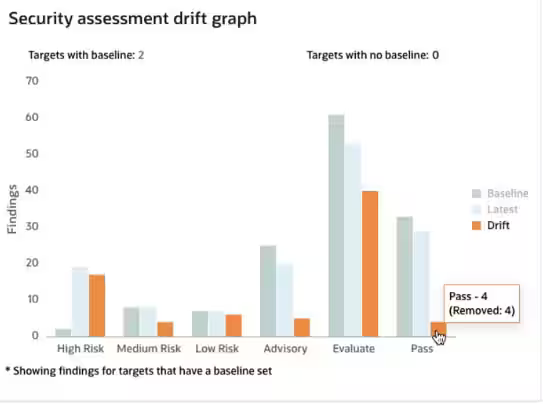
In AVDF 20.9 and 20.10, we introduced fleet-wide security assessment and drift management, respectively. AVDF 20.11 now allows you to quickly see how the security posture of all your Oracle databases is changing by introducing the security assessment drift chart. The chart on the auditor’s dashboard compares the latest assessment with the defined baseline for all databases and quickly identifies any drift requiring attention.
Figure 5: Security Assessment Drift Chart
More updates with AVDF 20.11
AVDF 20.11 introduces many other significant enhancements and features to improve your AVDF experience. Some of them are listed below.
Expanding support for tracking before/after values: AVDF currently collects before/after values from Oracle and Microsoft SQL Server databases and helps customers meet compliance requirements where they need to track the value change. AVDF 20.11 now extends the same before/after value change auditing support for MySQL, helping customers meet their compliance requirements for MySQL database also.
Finely scoped database firewall policies and reports: Until now, Database Firewall (DBFW) policies and reports were based on command groups such as DML, DDL, and DCL, and customers could not easily create policies on just a specific command. With AVDF 20.11, the command class has been expanded to commands such as DELETE, INSERT, UPDATE, DROP TABLE, etc. This enhancement helps you define narrow alert conditions and create unified reports – irrespective of whether the event data was from the audit logs or network-based SQL.
Use of global sets in all activity and GDPR reports: Until now, global sets of IP addresses, OS/DB users, sensitive objects, privileged users, and client programs have been used across Database Firewall policies, making it easier to apply the same rules. Starting in AVDF 20.11, you can now apply the same global set to filter all activity reports, including the compliance reports. For example, in GDPR compliance reports, you can use sensitive object sets to view user activity on sensitive data.
Audit trail migration: Customers have requested easy ways to migrate their audit trails to different agents due to aging agent hardware or the need for improved load balancing across agents. AVDF 20.11 provides flexibility to migrate the audit trail from one agent to another or agentless configuration and vice versa without losing any audit data and restarting the agent/trail.
AVDF certificate rotation from UI: AVDF uses certificates for internal communication among various services. The current process was lengthy and only partially automated. Now, with 20.11, you can have a clear picture of the certificate validity status from the AVDF console, and you can rotate these certificates with a single click when needed.
Source: oracle.com




0 comments:
Post a Comment